Unlocking Cybersecurity: Bridging Knowledge and Action
In the dynamic landscape of our daily routines and specialized IT training, a fundamental question emerges—do we merely absorb insights or actively shape our digital defenses? The realm of cybersecurity places a significant weight on the choices we make, as they can profoundly impact our digital well-being. Join me on a journey as we explore the bridge between knowledge and action, unraveling the pivotal role we play in fortifying our online security.
The Guardian: Your Password in the Digital Landscape
Your password, once a simple line of defense, has transformed into the primary bastion against potential cyber threats in today’s digital age. A mere string of characters is no longer sufficient, especially with the ever-evolving technology landscape. To enhance the security shield around your sensitive information, consider the strategic infusion of special characters, numbers, and an extended password length. However, the plot thickens when we confront the peril of password reuse—an Achilles’ heel that compromises even the most impeccable of passwords across multiple platforms.
Navigating Complexity: Passwords in the Cybersecurity Realm
The emphasis on password complexity in the intricate realm of cybersecurity is more crucial than ever before. The days when Password1, heading5678, or liliana2023! could safeguard our digital realms are long gone. In today’s interconnected landscape, where personal information sprawls across social media platforms, the risks tied to passwords linked to such details have escalated to unprecedented heights.
Embark with me on a journey below, where a carefully curated collection of password examples awaits, designed to transcend predictability and elevate your password complexity game. Dive into the world of Multi-Factor Authentication (MFA) methods—an added layer of security ensuring your digital gateways remain impenetrable in the ever-evolving face of cyber threats.
Consider the potency of word phrases like “liliana-ismywonderful-daughter98,” showcasing the essence of a robust password. Alternatively, embrace the randomness of generated passwords, such as 4LC5W8SwH6QGMP7xYA.
Explore a visually compelling chart provided by Hive Systems, offering insights into the time it takes for a password to succumb to compromise.
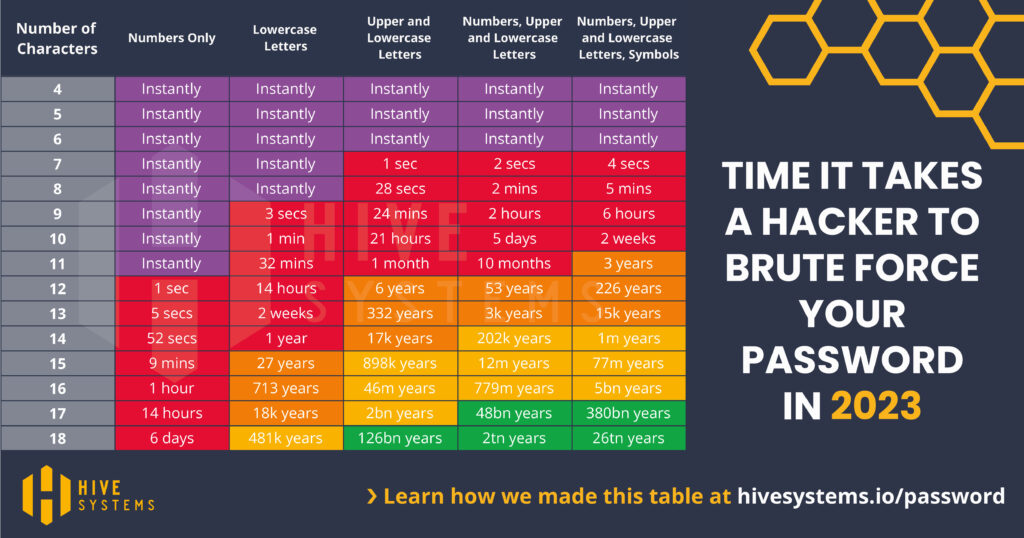
But amidst the complexity, a question arises: How can one manage these intricate and seemingly inconvenient passwords? Enter password managers like Nordpass—a glimpse into the future of password security. Tailored to alleviate the burden of memorization, these programs empower you to stay in control of your digital keys.
And here’s a golden nugget: Never underestimate the power of Multi-Factor Authentications (MFAs). Every opportunity to enable MFA is a crucial step toward fortifying your accounts, adding an extra layer of security in the event of a password compromise. The future of cybersecurity is intricate, but armed with the right tools and knowledge, you can navigate it with confidence. Let’s unlock the potential of a secure digital future together.
